Windows Defender Application Control (WDAC) Implementation - Part 4: Putting It All Together
Part 4 in a guide to setting up Windows Defender Application Control (WDAC)

Now that we have our three policy files, we now need to deploy them to our devices.
- Create two groups in EntraID:
- "WDAC Users" - we'll apply the two base policies to all users
- "WDAC Users - Postman" - this policy will apply to a subset of users in the "WDAC Users" group, as the Postman policy requires the base policy to work
- Populate the groups with some test user accounts. Ensure that any user in the "WDAC Users - Postman" group is in the "WDAC Users" group
- Convert the policy files to binary .p7b files by running the following PowerShell commands:
ConvertFrom-CIPolicy -XmlFilePath DefaultWindows_Enforced.xml -BinaryFilePath DefaultWindows_Enforced.p7b
ConvertFrom-CIPolicy -XmlFilePath BaseSupplemental.xml -BinaryFilePath BaseSupplemental.p7b
ConvertFrom-CIPolicy -XmlFilePath Postman.xml -BinaryFilePath Postman.p7b- The policies are now ready for deployment in Intune
Deploy the base policies
- Create a new custom policy in Intune named "WDAC - Base Policy"
- Add a new OMA-URI:
- Name:
Base Policy - OMA-URI:
./Vendor/MSFT/ApplicationControl/Policies/<BasePolicyID>/Policy - Data type:
Base64 (file) - Upload the file
DefaultWindows_Enforced.p7b
- Name:
- Add a new OMA-URI:
- Name:
Supplemental Base Policy - OMA-URI:
./Vendor/MSFT/ApplicationControl/Policies/<SupplementalBasePolicyID>/Policy - Data type: Base64 (file)
- Upload the file
BaseSupplemental.p7b
- Name:
<BasePolicyID> and <SupplementalBasePolicyID> with the PolicyID from each XML file- Assign the policy to the group "WDAC Users"
As the policies deploy to the users in the group, the policy files will begin to appear in C:\Windows\System32\CodeIntegrity\CIPolicies\Active
You can also monitor events in Event Viewer under the path Applications and Services Logs > Microsoft > Windows > Code Integrity > Operational
Deploy the Postman policy
- Create a new custom policy in Intune named "WDAC - Postman"
- Add a new OMA-URI:
- Name:
Base Policy - OMA-URI:
./Vendor/MSFT/ApplicationControl/Policies/<PostmanPolicyID>/Policy - Data type:
Base64 (file) - Upload the file
Postman.p7b
- Name:
<PostmanPolicyID> with the PolicyID from the Postman.xml file- Assign the policy to the group "WDAC Users - Postman"
Testing
On any computer that the policies have been deployed to, attempt to download and run any software - a good example is the Firefox installer, as it can install Firefox system wide, or to the user profile if the user doesn't have local admin privileges.
When attempting to run the Firefox installer, an error message similar to the following should appear:
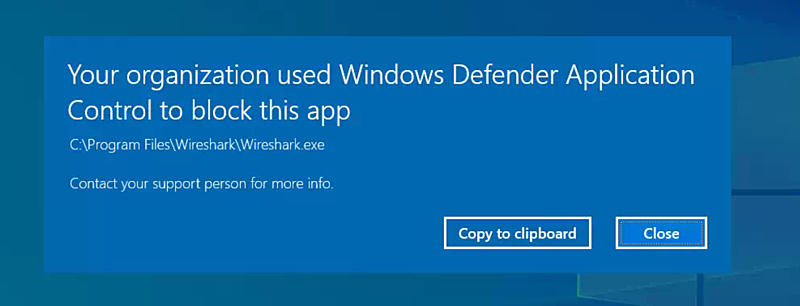
A dialog similar to the above should appear for any exe that doesn't have a policy that allows it.
Now attempt to start Postman, if the policy was applied correctly it should simply start without error.
Adding support for other apps
Anytime you need to add support for new apps, simply follow the same instructions for creating the Postman policy (substituting names and paths as appropriate), and deploy to the user groups of your choice.
This sort of configuration makes it easy to limit permission to run a specific to a specific set of users. I generally use the same group that is used to deploy the app to the users device.
